Oracle JDBC Drivers release 10.2.0. And Distribution License Agreement to download. Oracle Database 10g Release 2 (10.2.0.4).
The Type 4 JDBC drivers from DataDirect provide JDBC high-performance access through Oracle CEP to industry-leading data stores across the Internet and intranets. The Type 4 JDBC drivers are optimized for the Java environment, allowing you to incorporate Java technology and extend the functionality and performance of your existing system.
The Oracle CEP Type 4 JDBC drivers from DataDirect are proven drivers that:
- Support performance-oriented and enterprise functionality such as distributed transactions, savepoints, multiple open result sets and parameter metadata.
- Are Java EE Compatibility Test Suite (CTS) certified and tested with the largest JDBC test suite in the industry.
- Include tools for testing and debugging JDBC applications.
The following sections provide more information about the Type 4 JDBC drivers:
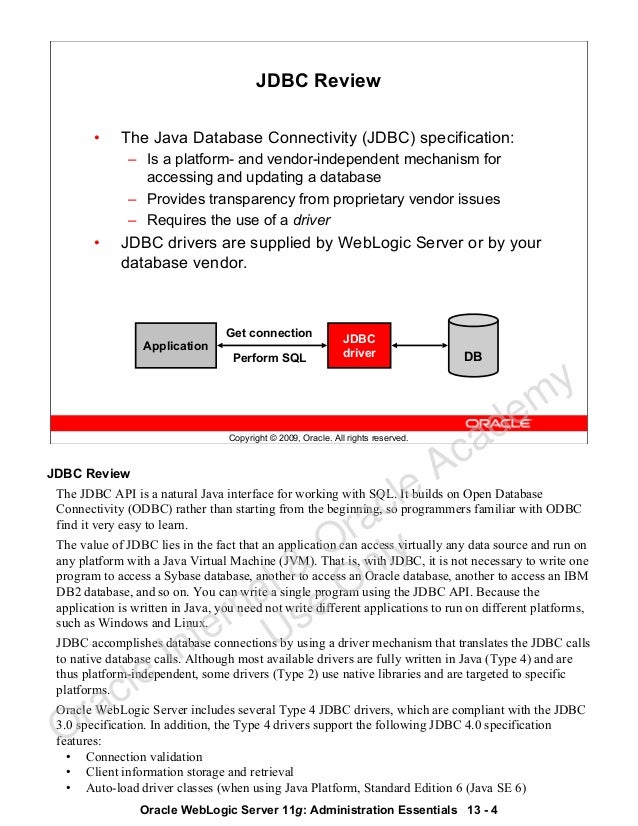
JDBC Specification Compliance
The Type 4 JDBC drivers are compliant with the JDBC 3.0 specification In addition, the Type 4 JDBC drivers support the following JDBC 4.0 specification features:
- Connection validation
- Client information storage and retrieval
- Auto-load driver classes (when using Java SE 6)
For details, see JDBC Support.
Installation
Type 4 JDBC drivers are automatically installed with Oracle CEP and are automatically added to your classpath on the server.
Supported Databases
Table 2-1 shows the databases supported by each of the Type 4 JDBC drivers.
Supported Databases |
|---|
|
Connecting Through JDBC Data Sources
To use the Type 4 JDBC drivers, you create a JDBC data source in your Oracle CEP configuration and select the JDBC driver to create the physical database connections in the data source. Applications can then look up the data source on the JNDI tree and request a connection.
For information about JDBC and data sources in Oracle CEP, see Configuring Access to a Relational Database.
Specifying Connection Properties
You specify connection properties for connections in a data source Oracle CEP config.xml file. Connection properties vary by DBMS. For the list of the connection properties specific to each Type 4 JDBC driver, see the appropriate driver chapter:
- For the MS SQL Server driver, see SQL Server Connection Properties.
Limiting Connection Creation Time with LoginTimeout
When creating database connections in a JDBC data source, if the database is unavailable, the request may hang until the default system timeout expires. On some systems this can be as long as 9 minutes. The request will hang for each connection in the JDBC data source. To minimize this hang time, you can specify a LoginTimeout value for the connection. All Type 4 JDBC Drivers support the LoginTimeout connection property. When you specify a LoginTimeout connection property and the connection is not created immediately, the request waits for the time you specify. If the connection cannot be created within the time specified, the driver throws an SQL exception.
For details on configuring connection properties, see the appropriate driver chapter:
Using IP Addresses
The Type 4 JDBC drivers support Internet Protocol (IP) addresses in IPv4 and IPv6 format. IPv6 addresses are only supported when connecting to certain database versions (as shown in Table 2-2). In addition, to connect to IPv6 addresses, the driver machine requires J2SE 5.0 or higher on Windows and J2SE 1.4 on UNIX/Linux.
IPv4 | |
|---|---|
Microsoft SQL Server | Microsoft SQL Server 2005 and higher |
If your network supports named servers, the server name specified in the connection URL or data source can resolve to an IPv4 or IPv6 address. Alternatively, you can specify addresses using IPv4 or IPv6 format in the server name portion of the connection URL. You also can specify addresses in either format using the ServerName data source property.
| Note: | When specifying IPV6 addresses in a connection URL or data source property, the address must be enclosed by brackets. |
In addition to the normal IPv6 format, the Type 4 JDBC drivers support IPv6 alternative formats for compressed and IPv4/IPv6 combination addresses.
For complete information about IPv6, go to the following URL:

http://tools.ietf.org/html/rfc4291#section-2.2
Using Security
The Type 4 JDBC drivers support the following security features: authentication and data encryption.
Authentication
On most computer systems, a password is used to prove a user's identity. This password often is transmitted over the network and can possibly be intercepted by malicious hackers. Because this password is the one secret piece of information that identifies a user, anyone knowing a user's password can effectively be that user. Authentication methods protect the identity of the user. Type 4 JDBC drivers support the following authentication methods:
- User ID/password authentication authenticates the user to the database using a database user name and password.
- Kerberos is a trusted third-party authentication service. The drivers support both Windows Active Directory Kerberos and MIT Kerberos implementations for Oracle. For SQL Server, the driver supports Windows Active Directory Kerberos only.
- Client authentication uses the user ID of the user logged onto the system on which the driver is running to authenticate the user to the database. The database server relies on the client to authenticate the user and does not provide additional authentication.
- NTLM authentication is a single sign-on authentication method for Windows environments. This method provides authentication from Windows clients only.
Table 2-3 shows the authentication methods supported by the Type 4 JDBC drivers.
UserID/ Password | Client |
|---|---|
Microsoft SQL Server | X1 |
1Supported for Microsoft SQL Server 2000 and higher. |
Kerberos Authentication Requirements
Verify that your environment meets the requirements listed in Table 2-4 before you configure your driver for Kerberos authentication.
Requirements |
|---|
The database server must be running one of the following databases:
|
The Kerberos server is the machine where the user IDs for authentication are administered. The Kerberos server is also the location of the Kerberos Key Distribution Center (KDC). If using Windows Active Directory, this machine is also the domain controller. Network authentication must be provided by Windows Active Directory on one of the following operating systems:
|
J2SE 1.4.2 or higher must be installed. |
To use Kerberos authentication, some configuration is required after installation of the JDBC Type 4 drivers. See the individual driver chapters for details about configuring authentication.
NTLM Authentication Requirements
Verify that your environment meets the requirements listed in Table 2-5 before you configure the driver for NTLM authentication.
Requirements |
|---|
The database server must be administered by the same domain controller that administers the client and must be running one of the following databases:
|
The domain controller must administer both the database server and the client. Network authentication must be provided by NTLM on one of the following operating systems:
|
The client must be administered by the same domain controller that administers the database server and must be running on one of the following operating systems:
In addition, J2SE 1.3 or higher must be installed. |
To use NTLM authentication, minimal configuration is required after installation of the JDBC Type 4 drivers. See the individual driver chapters for details about configuring authentication.
Data Encryption Across the Network
If your database connection is not configured to use data encryption, data is sent across the network in a format that is designed for fast transmission and can be decoded by interceptors given some time and effort. Because this format does not provide complete protection from interceptors, you may want to use data encryption to provide a more secure transmission of data. For example, you may want to use data encryption in the following scenarios:
- You have offices that share confidential information over an intranet.
- You send sensitive data, such as credit card numbers, over a database connection.
- You need to comply with government or industry privacy and security requirements.
| Note: | Data encryption may adversely affect performance because of the additional overhead (mainly CPU usage) required to encrypt and decrypt data. |
Type 4 JDBC drivers support the following encryption method:
- Secure Sockets Layer (SSL). SSL is an industry-standard protocol for sending encrypted data over database connections. SSL secures the integrity of your data by encrypting information and providing client/server authentication.
Table 2-6 shows the data encryption methods supported by the Type 4 JDBC drivers.
Database-Specific |
|---|
Microsoft SQL Server |
1Supported for Microsoft SQL Server 2000 and higher. |
SSL Encryption
SSL works by allowing the client and server to send each other encrypted data that only they can decrypt. SSL negotiates the terms of the encryption in a sequence of events known as the SSL handshake. The handshake involves the following types of authentication:
- SSL server authentication requires the server to authenticate itself to the client.
- SSL client authentication is optional and requires the client to authenticate itself to the server after the server has authenticated itself to the client.
See the individual driver chapters for details about configuring SSL.
SSL Server Authentication
When the client makes a connection request, the server presents its public certificate for the client to accept or deny. The client checks the issuer of the certificate against a list of trusted Certificate Authorities (CAs) that resides in an encrypted file on the client known as a truststore. Optionally, the client may check the subject (owner) of the certificate. If the certificate matches a trusted CA in the truststore (and the certificate’s subject matches the value that the application expects), an encrypted connection is established between the client and server. If the certificate does not match, the connection fails and the driver throws an exception.
To check the issuer of the certificate against the contents of the truststore, the driver must be able to locate the truststore and unlock the truststore with the appropriate password. You can specify truststore information in either of the following ways:
- Specify values for the Java system properties javax.net.ssl.trustStore and javax.net.ssl.trustStorePassword. For example:
- Specify values for the connection properties TrustStore and TrustStorePassword. For example:
and
This method sets values for all SSL sockets created in the JVM.
and
Any values specified by the TrustStore and TrustStorePassword properties override values specified by the Java system properties. This allows you to choose which truststore file you want to use for a particular connection.
Alternatively, you can configure the Type 4 JDBC drivers to trust any certificate sent by the server, even if the issuer is not a trusted CA. Allowing a driver to trust any certificate sent from the server is useful in test environments because it eliminates the need to specify truststore information on each client in the test environment. If the driver is configured to trust any certificate sent from the server, the issuer information in the certificate is ignored.
Required Permissions for the Java Security Manager
Using the Type 4 JDBC drivers with the Java Security Manager enabled requires certain permissions to be set in the security policy file of the domain. WebLogic Server provides a sample security policy file that you can edit and use. The file is located at WL_HOMEserverlibweblogic.policy. The weblogic.policy file includes all necessary permissions for the drivers except for access to temporary files and access to tnsnames.ora. If you use the weblogic.policy file without changes, you may not need to grant any further permissions. If you use another security policy file or if you use driver features that require additional permissions, see the following sections for details about required permissions.
| Note: | Web browser applets running in the Java 2 plug-in are always running in a JVM with the Java Security Manager enabled. |
Permissions for Establishing Connections
To establish a connection to the database server, the Type 4 JDBC drivers must be granted the permissions as shown in the following examples. You must grant permissions to the wlbase.jar and wlutil.jar files as well as the jar for your specific database management system. You can grant the permissions to all JAR files in the directory or just to the specific files.
For all JAR files in the directory:
For individual JAR files:
And one or more of the following:
where WL_HOME is the directory in which you installed WebLogic Server.
In addition, if Microsoft SQL Server named instances are used, permission must be granted for the listen and accept actions as shown in the following example:
Granting Access to Java Properties
To allow the Type 4 JDBC drivers to read the value of various Java properties to perform certain operations, permissions must be granted as shown in the following example:
where WL_HOME is the directory in which you installed WebLogic Server.
You can also grant these permissions to individual files as shown in Permissions for Establishing Connections.
Granting Access to Temporary Files
Access to the temporary directory specified by the JVM configuration must be granted in the security policy file, typically in the security policy file used by the JVM in the JAVA_HOME/jre/lib/security folder. To use insensitive scrollable cursors or to perform client-side sorting of DatabaseMetaData result sets, all code bases must have access to temporary files. The following example shows permissions that have been granted for the C:TEMP directory:
where WL_HOME is the directory in which you installed WebLogic Server.
You can also grant these permissions to individual files as shown in Permissions for Establishing Connections.
Permissions for Kerberos Authentication
To use Kerberos authentication with the Type 4 JDBC drivers that support it, the application and driver code bases must be granted security permissions in the security policy file of the Java 2 Platform as shown in the following examples.
For more information about using Kerberos authentication with the Type 4 JDBC drivers, see the appropriate driver chapters.
Microsoft SQL Server
where:
WL_HOMEis the directory in which you installed WebLogic Server.your_realmis the Kerberos realm (or Windows Domain) to which the database host machine belongs.db_hostnameis the host name of the machine running the database.SQLServer_portis the TCP/IP port on which the Microsoft SQL Server instance is listening.
Unicode Support
Multi-lingual applications can be developed on any operating system platform with JDBC using the Type 4 JDBC drivers to access both Unicode and non-Unicode enabled databases. Internally, Java applications use UTF-16 Unicode encoding for string data. When fetching data, the Type 4 JDBC drivers automatically perform the conversion from the character encoding used by the database to UTF-16. Similarly, when inserting or updating data in the database, the drivers automatically convert UTF-16 encoding to the character encoding used by the database.
The JDBC API provides mechanisms for retrieving and storing character data encoded as Unicode (UTF-16) or ASCII. Additionally, the Java string object contains methods for converting UTF-16 encoding of string data to or from many popular character encodings.
Error Handling
The Type 4 JDBC drivers report errors to the calling application by throwing SQLExceptions. Each SQLException contains the following information:
- Description of the probable cause of the error, prefixed by the component that generated the error
- Native error code (if applicable)
- String containing the XOPEN SQLstate
Driver Errors
An error generated by a Type 4 JDBC driver has the following format:
For example:
You may need to check the last JDBC call your application made and refer to the JDBC specification for the recommended action.
Database Errors
An error generated by the database has the following format:
For example:
Use the native error code to look up details about the possible cause of the error. For these details, refer to your database documentation.
| © BEA Systems |
I have installed Oracle 10G XE. I want to connect to it using JDBC . Which driver should i use for it and from where can i download it ?
Thank You.
4 Answers
On the machine you have installed the server, Oracle JDBC drivers are in ORACLE_HOME/jdbc/lib. Just put ojdbc14.jar on your classpath (ojdbc14_g.jar is the same as ojdbc14.jar, except that classes were compiled with 'javac -g' and contain some tracing information).
EDIT: According to Oracle Database 10g Release 2 (10.2.0.4) JDBC Drivers, ojdbc14.jar contains classes for use with JDK 1.4 and 1.5 (and I don't see why it wouldn't work with a JDK 6, some features of JDBC 4.0 won't just be available).
Some newer drivers are available at Oracle Database 11g Release 2 JDBC Drivers but I don't really see the difference between ojdbc14.jar and ojdbc15.jar (except that ojdbc15.jar requires a JDK 5+): they are both JDBC 3.0 driver so I think it's just a matter of end of life support for ojbdc14.jar. If you want JDBC 4.0 support, you'll need ojdbc16.jar though. Have a look at the Oracle JDBC FAQ if you want more details.
You generally want the latest JDBC drivers, they will work with older versions of the database as well. Or, to be on the safe side, match the JDBC version with your DB.
ThiloThiloAccording to this getting started guide you need the Oracle Express client which can be found here
Mark WilkinsMark WilkinsYou want to choose a JDBC driver that matches both your version of Oracle and the JDK you're using. ojdbc14.jar is for JDK 1.4; there are newer versions for at least JDK 5 that I know of. I'm not sure if there's a JDBC driver for JDK 6. Use the best match to your situation that Oracle makes available.
duffymo